
- Why Regular Data Recovery Tools Can’t Restore Files from RAID
- Key Information About the NAS QNAP TBS-464
- How to Remove Hard Disks from Your NAS and Connect Them to a PC
Why Regular Data Recovery Tools Can’t Restore Files from RAID
Conventional hard drives store user data by writing it sequentially across the disk surface, which means an entire file is typically located on a single drive. In contrast, when data is written to a RAID array, each file is split into multiple fragments. These fragments are then distributed and written in sequence across all the drives in the array. Depending on the configuration, fragment sizes can range from 2 KB to 2 MB, so every file is physically stored across several disks at once.
This approach significantly increases read and write performance — after all, writing two halves of a 1 GB file to two drives simultaneously is much faster than writing the full 1 GB to a single disk. However, this same mechanism makes file recovery far more complex.
Different RAID levels use different methods to distribute and protect data. On top of that, manufacturers like QNAP often add their own proprietary structures and variations. As a result, data can be written to disks in many different formats, and each requires a specific approach during recovery.
How can the number of drives in a NAS QNAP TBS-464 device's RAID array impact data recovery and potential loss?
The number of drives in a NAS QNAP TBS-464 device's RAID array can impact data recovery and potential loss in the following ways:
- Redundancy: RAID arrays are designed to provide redundancy by distributing data across multiple drives. The more drives in the array, the higher the level of redundancy. This means that even if one or more drives fail, the data can still be recovered from the remaining drives. With fewer drives in the array, the level of redundancy decreases, increasing the risk of data loss.
- Fault tolerance: RAID arrays use various RAID levels (such as RAID 0, RAID 1, RAID 5, RAID 6, etc.) to provide different levels of fault tolerance. Each RAID level has a specific number of drives required to operate. If the number of drives in the array falls below the required minimum, the RAID array may become non-functional, leading to potential data loss.
- Rebuilding process: When a drive fails in a RAID array, the array needs to rebuild the data onto a replacement drive. This process involves reading data from the remaining drives and reconstructing the data on the new drive. With more drives in the array, the rebuilding process can be faster and less resource-intensive. However, with fewer drives, the rebuilding process can take longer, increasing the risk of a second drive failure during the rebuild, which can result in complete data loss.
- Performance: The number of drives in a RAID array can also impact its performance. With more drives, the array can distribute the workload across multiple drives, resulting in faster data access and transfer speeds. However, with fewer drives, the performance may be slower, affecting data recovery and overall system performance.
In summary, having a sufficient number of drives in a NAS QNAP TBS-464 device's RAID array is crucial for maintaining data integrity, ensuring fault tolerance, and minimizing the risk of data loss during drive failures.
How to Remove Hard Disks from Your NAS and Connect Them to a PC
Although the NAS TBS-464 can be accessed over the network, you still need to remove its hard disks and connect them directly to a Windows PC. Only then can the recovery software properly scan and analyze the drives. Follow these steps:
-
Power off the NAS and disconnect it from the power source.
WARNING! Before removing any drives, carefully read the device manual. Improper actions may damage both the NAS enclosure and the hard disks in the RAID array.
-
Remove the hard disks one by one, gently sliding each drive out of its slot. Remember that hard disks are highly sensitive: any impact or drop can cause serious physical damage.
-
Label each hard disk according to its position inside the NAS. The order of the drives is crucial for correct RAID reconstruction.
-
Connect the drives to your computer. In this video, we explain which ports you can use to connect hard disks and what to do if your PC does not have enough free connectors.
Go to view
Step-by-Step Data Recovery with Hetman RAID Recovery
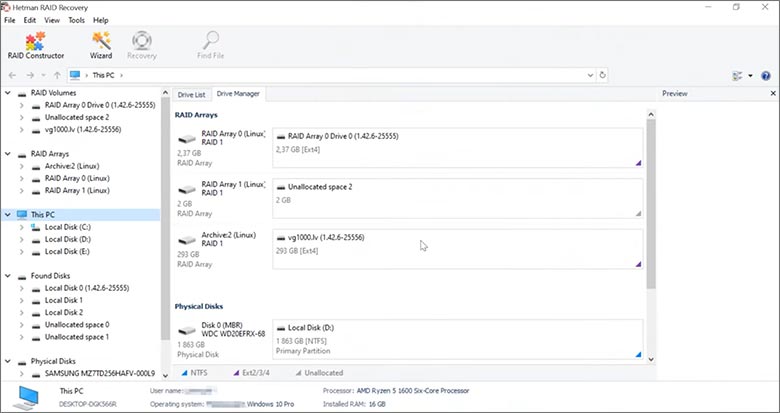
This program restores data from damaged RAID arrays and is fully compatible with QNAP TBS-464. Each hard disk in the array contains technical metadata describing how files were written. When launched, Hetman RAID Recovery analyzes this metadata, automatically reconstructs the damaged array, and provides access to its contents. After that, you can browse the recovered disk and save your files. The program can also restore files that were accidentally deleted from the network drive.

How to recover data from a QNAP
TBS-464 has 4 HDD slots, and it supports the following array types:
- RAID 6;
- RAID 5;
- RAID 10;
- RAID 0;
- RAID 1;
- JBOD;
NAS supports:
- ZFS;
- EXT4;
- EXT3;
- exFAT;
- FAT32 (External Disk Only);
- NTFS (External Disk Only);
- HFS+ (External Disk Read Only);
How to Safely Recover Data from Disk Images
This utility allows you to create a complete copy of a disk and work with the disk image instead of the physical drive. This approach helps protect your data from:
- Overwriting during the recovery process;
- Additional data loss caused by bad sectors;
- User errors.
To create a disk image, follow these steps:
-
Ensure you have enough free space to store the image. Its size will typically match the size of the original disk.
-
In the main window, select the target disk and choose Tools - Save Disk. You can also select multiple disks if needed.
-
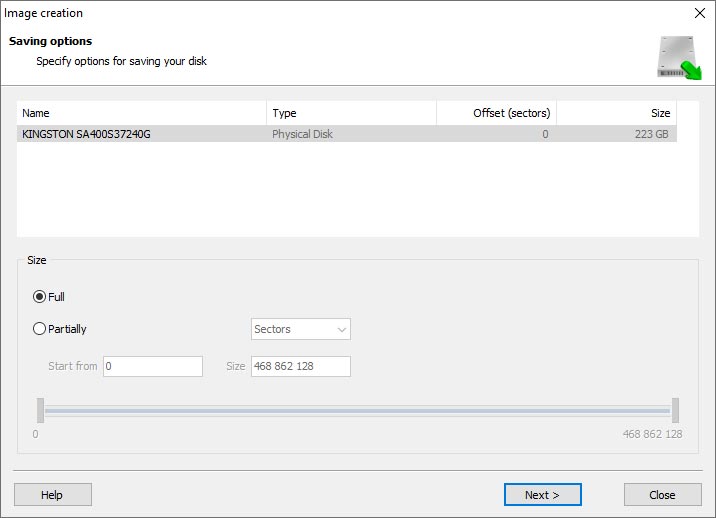
When the Image Creation Wizard opens, select whether you want to save the entire disk or only a specific region. Adjust the settings and click Next.
-
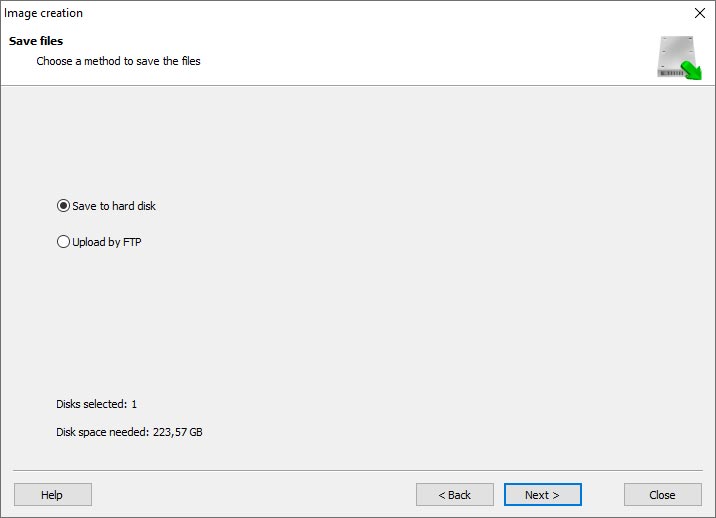
Choose the directory where the image will be saved. You may select any available disk connected to your PC or upload the image via FTP.
Where Are the User’s Files Actually Stored?
The QNAP TBS-464 network-attached storage keeps QTS (QuTS hero) operating system files on a separate RAID 1 (mirrored) array. Usually, all NAS systems create several volumes on every hard disk, and the first of them takes up to 2 Gb of space. This is where operating system files are stored. Other volumes are united into a RAID array where user’s data is written.
RAID Recovery Software: Detailed Comparison
| Product | Operating system | RAID controller support | Supported file systems | Virtual RAID controller support | Data recovery from damaged RAID | File preview |
|---|---|---|---|---|---|---|
| Hetman RAID Recovery | Windows, Linux, MacOS | Yes, over 100 controllers | FAT, exFAT, NTFS, ReFS, APFS, HFS+, Ext4, Ext3, Ext2, ReiserFS, Btrfs, VMFS, Hikvision, XFS, UFS, ZFS | Yes | Yes | Yes |
| DiskInternals RAID Recovery | Windows | Yes, over 10 controllers | FAT, NTFS, Ext2/3/4, HFS+ | No | Yes | Yes |
| R-Studio | Windows, Mac, Linux | Yes, over 20 controllers | FAT, NTFS, Ext2/3/4, HFS+ | Yes | Yes | Yes |
| UFS Explorer RAID Recovery | Windows, Mac, Linux | Yes, over 100 controllers | FAT, NTFS, Ext2/3/4, HFS+ | Yes | Yes | Yes |
| EaseUS Data Recovery | Windows | Yes, over 20 controllers | FAT, NTFS, Ext2/3/4, HFS+ | No | Yes | Yes |
| ReclaiMe Free RAID Recovery | Windows | Yes, over 100 controllers | FAT, NTFS, Ext2/3/4, HFS+ | Yes | Yes | Yes |




Yes, it is possible to recover data from a NAS QNAP TBS-464 device that has suffered a power loss or sudden shutdown. However, the success of data recovery depends on the extent of the damage and the condition of the device.
Here are some steps you can take to attempt data recovery:
It's important to note that attempting data recovery on your own can be risky and may further damage the device or the data. It is recommended to consult with a professional data recovery service if the data is critical or valuable.