- What Are Common Causes of .REQ Files Lost or Failure?
- How to recover lost .REQ files?
- Programs to recover .REQ files
- How to open file with .REQ extension?
What Are Common Causes of ".REQ" Files Lost or Failure?
Some common causes of ".REQ" files being lost or failing include:
- Accidental deletion: Users may accidentally delete ".REQ" files while organizing or cleaning up their computer's storage.
- System crashes: Sudden system crashes or power outages can result in the loss or corruption of ".REQ" files.
- Software or hardware issues: Issues with software applications or hardware components, such as a faulty hard drive or incompatible software, can lead to ".REQ" file loss or failure.
- Virus or malware attacks: Malicious software can infect and damage ".REQ" files, making them inaccessible or corrupt.
- File system errors: Errors within the file system, such as disk errors or file system corruption, can cause ".REQ" files to become lost or unreadable.
- Improper file transfer: If ".REQ" files are not transferred correctly during file sharing or copying processes, they may become lost or corrupted.
- Formatting or partitioning errors: Formatting or partitioning a storage device without proper backup can result in the loss of all files, including ".REQ" files.
- Software conflicts: Conflicts between different software applications or incompatible software versions can cause issues with ".REQ" files.
- Human error: Accidental overwriting, renaming, or moving of ".REQ" files by users can lead to their loss or failure.
- Hardware failure: Hardware components, such as a failing hard drive or memory module, can cause ".REQ" files to become lost or inaccessible.
How to recover lost ".REQ" files?
Sometimes while working with a computer, laptop or other stationary or mobile devices, you may encounter various bugs, freezes, hardware or software failures, even in spite of regular updates and junk cleaning. As a result, an important ".REQ" file may be deleted.

🧺 How to Recover Files and Folders After Sending Them to the Recycle Bin and Deleting? (Windows 11)
By no means should you think that the only way to recover a ".REQ" file is always to create it once more.
Use programs for recovering ".REQ" files if a file was lost after accidental or deliberate deleting, formatting the memory card or the internal storage, cleaning the storage device, after a virus attack or a system failure.
Programs to recover ".REQ" files
Looking for a way to get files back? In cases when files were deleted and they cannot be restored by using standard operating system tools, use Hetman Partition Recovery.
Follow the directions below:
-
Download Hetman Partition Recovery, install and start the program.
-
The program will automatically scan the computer and display all hard disks and removable drives connected to it, as well as physical and local disks.
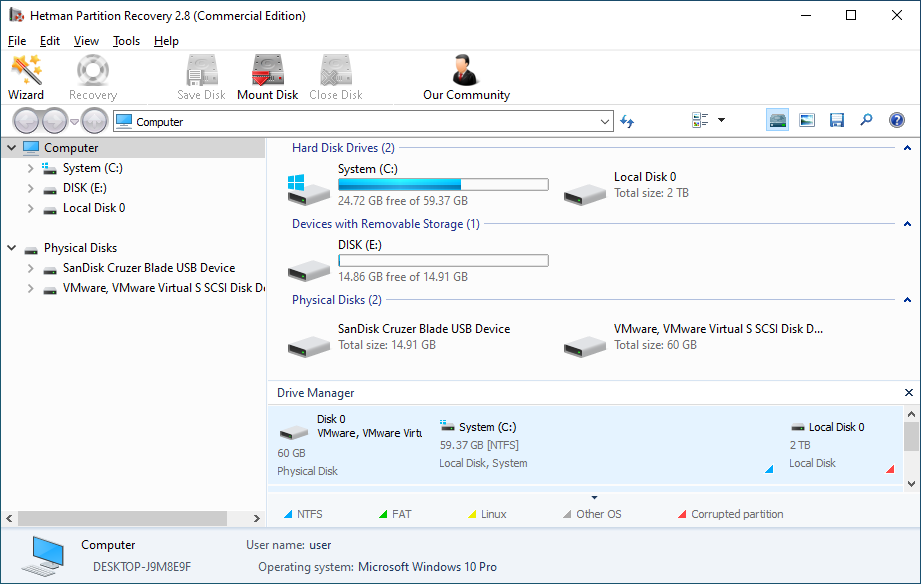
-
Double-click on the disk from which you need to recover ".REQ" files, and select analysis type.
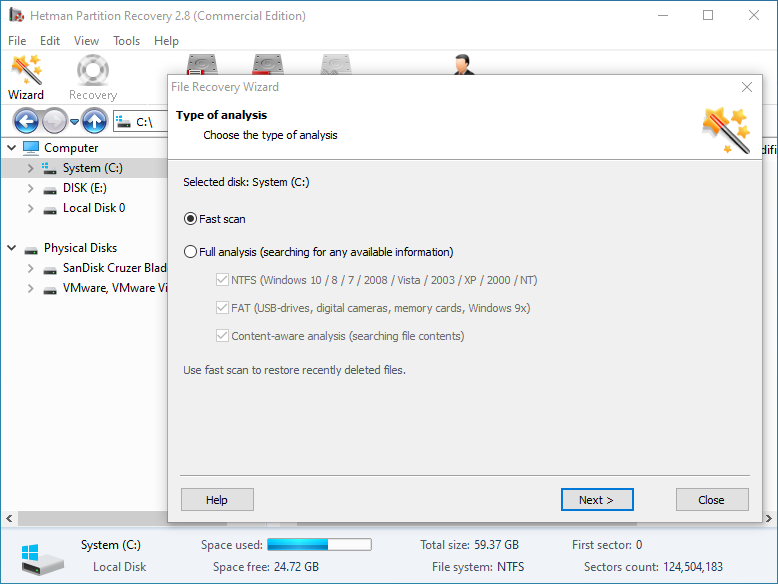
-
When the scanning is over, you will be shown the files for recovery.
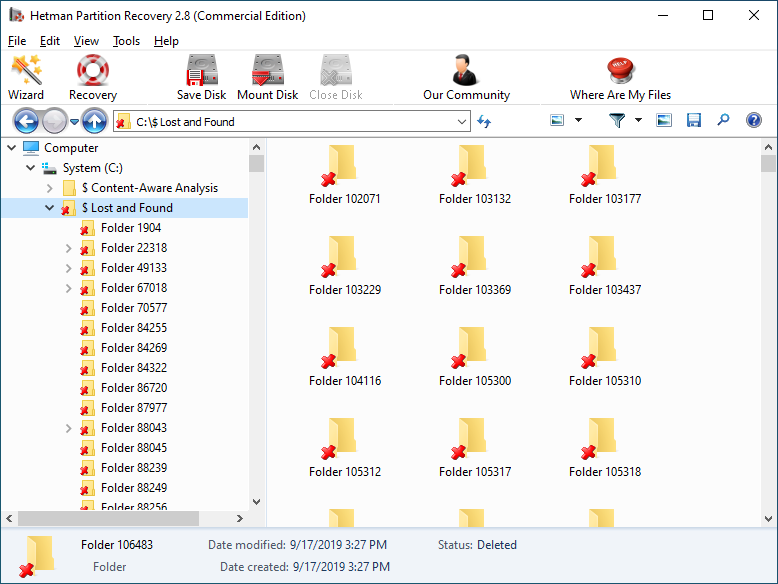
-
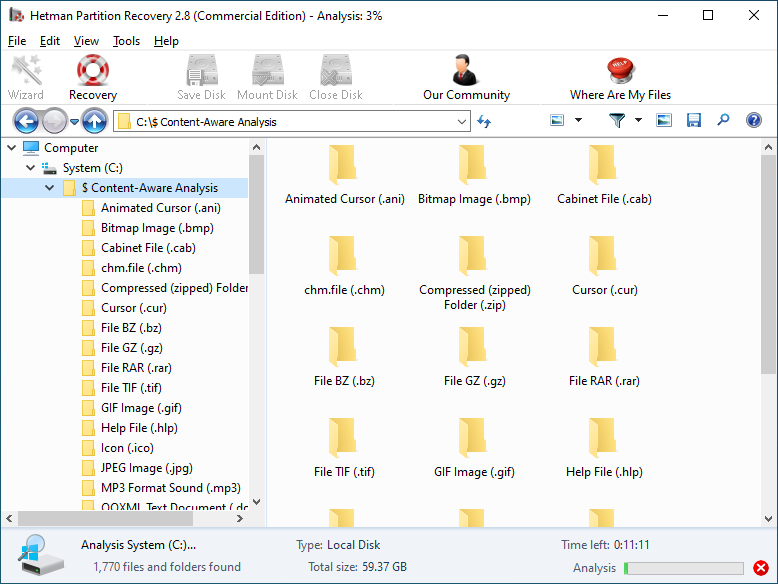
To find a file you need, use the program’s interface to open the folder it was deleted from, or go to the folder "Content-Aware Analysis" and select the required file type.
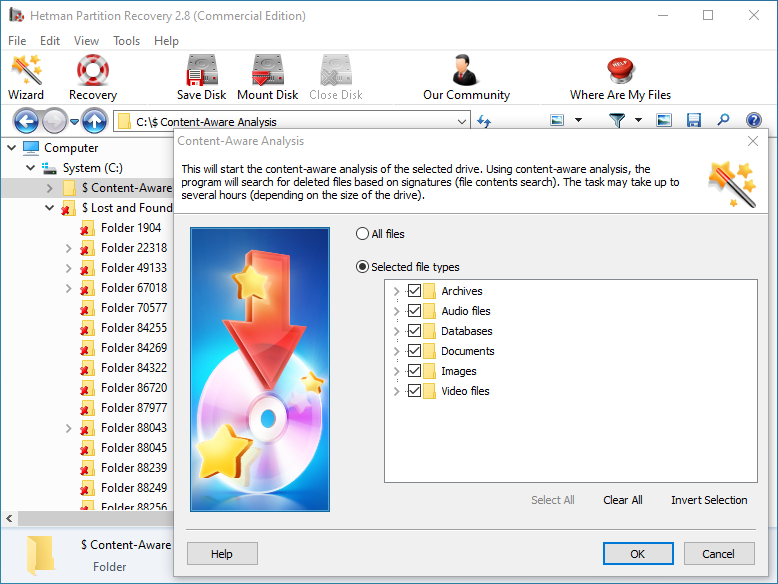
-
Select the files you have been looking for and click "Recovery".
-
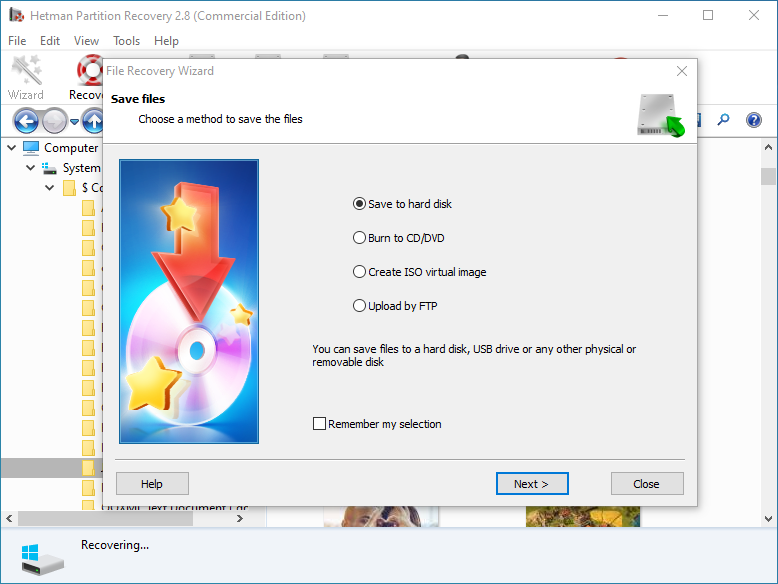
Choose one of the methods for saving the files and recover them.
How to open file with ".REQ" extension?
Looking for how to open a stereo canon SD Card Version Request File image file file?
Programs that open ".REQ" files
| Windows |
|---|
|
|
Additional Information
-
File type: Canon SD Card Version Request File
-
File extension: .REQ
-
Developer: Canon
-
Category: Misc Files
-
Format: N/A
-
File types that use the extension .REQ:
Canon SD Card Version Request File
SSL Certificate Request File



