- What Are Common Causes of .TLS Files Lost or Failure?
- How to recover lost .TLS files?
- Programs to recover .TLS files
- How to open file with .TLS extension?
What Are Common Causes of ".TLS" Files Lost or Failure?
There can be several common causes for ".TLS" files being lost or failing:
- Accidental deletion: Users may accidentally delete ".TLS" files while organizing or cleaning up their storage.
- Software or hardware issues: Issues with the software or hardware of the device where the ".TLS" files are stored can lead to their loss or failure. This includes system crashes, software bugs, or hardware failures.
- File system corruption: Corruption in the file system can result in the loss or failure of ".TLS" files. This can occur due to improper system shutdowns, malware infections, or disk errors.
- Formatting or partitioning: If a storage device is formatted or partitioned, it can erase all the data, including ".TLS" files, from the device.
- File transfer errors: Errors during the transfer of ".TLS" files, such as interruptions in network connectivity or incomplete transfers, can lead to their loss or failure.
- Virus or malware attacks: Viruses or malware can infect the device and cause damage to files, including ".TLS" files. They can corrupt or delete the files, making them inaccessible.
- Human error: Human error, such as accidental overwriting, renaming, or moving of ".TLS" files, can result in their loss or failure.
- Software conflicts: Conflicts between different software applications or incompatible software versions can cause issues with ".TLS" files, leading to their loss or failure.
- Physical damage: Physical damage to the storage device where the ".TLS" files are stored, such as dropping a hard drive or exposing it to extreme temperatures or moisture, can result in data loss.
It is important to have regular backups of ".TLS" files to prevent permanent loss in case of any of these causes.
How to recover lost ".TLS" files?
Sometimes while working with a computer, laptop or other stationary or mobile devices, you may encounter various bugs, freezes, hardware or software failures, even in spite of regular updates and junk cleaning. As a result, an important ".TLS" file may be deleted.

🧺 How to Recover Files and Folders After Sending Them to the Recycle Bin and Deleting? (Windows 11)
By no means should you think that the only way to recover a ".TLS" file is always to create it once more.
Use programs for recovering ".TLS" files if a file was lost after accidental or deliberate deleting, formatting the memory card or the internal storage, cleaning the storage device, after a virus attack or a system failure.
Programs to recover ".TLS" files
Looking for a way to get files back? In cases when files were deleted and they cannot be restored by using standard operating system tools, use Hetman Partition Recovery.
Follow the directions below:
-
Download Hetman Partition Recovery, install and start the program.
-
The program will automatically scan the computer and display all hard disks and removable drives connected to it, as well as physical and local disks.
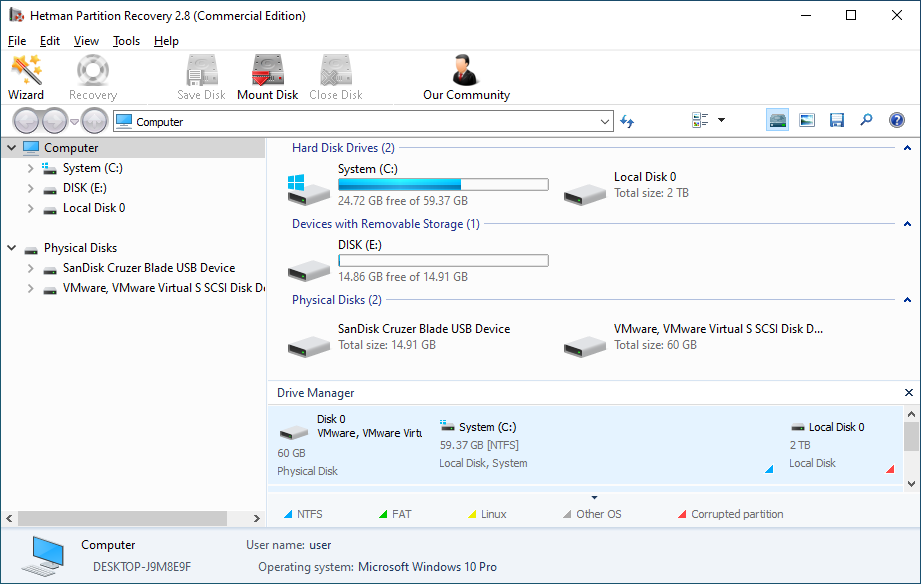
-
Double-click on the disk from which you need to recover ".TLS" files, and select analysis type.
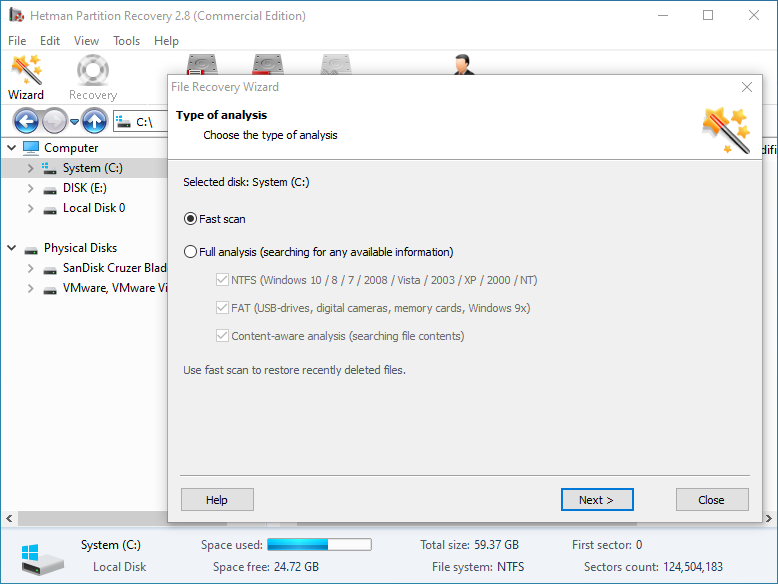
-
When the scanning is over, you will be shown the files for recovery.
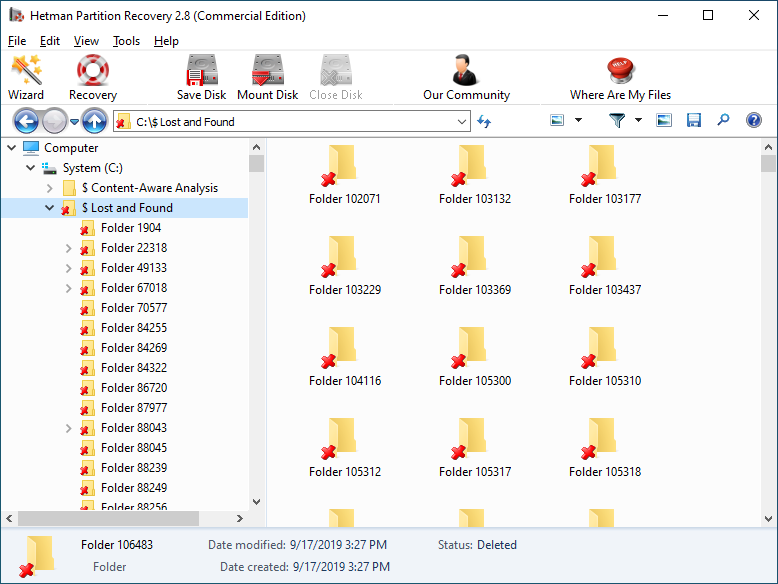
-
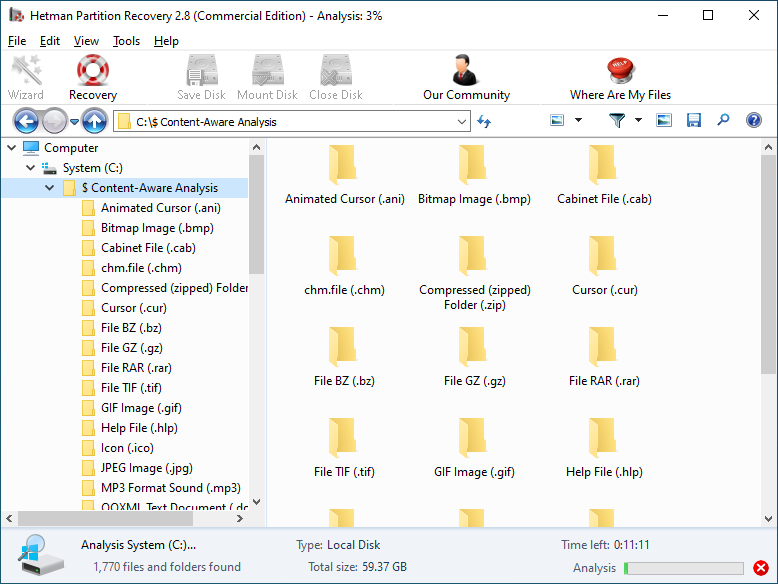
To find a file you need, use the program’s interface to open the folder it was deleted from, or go to the folder "Content-Aware Analysis" and select the required file type.
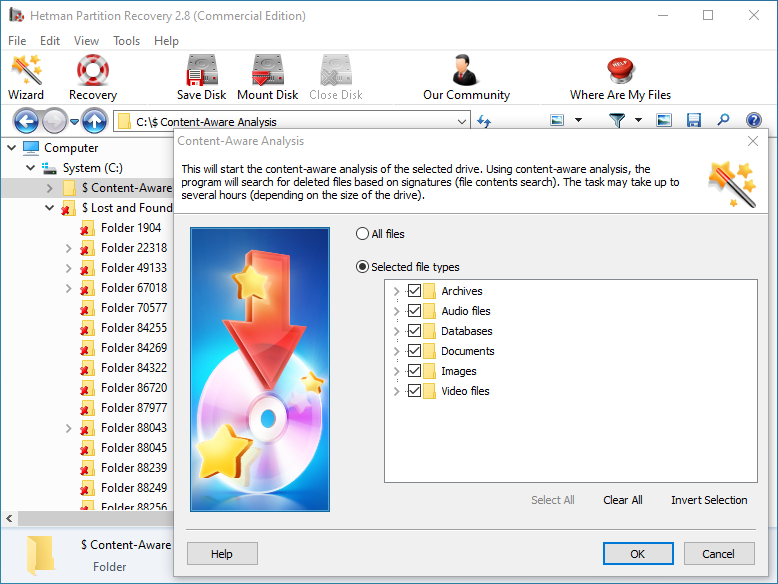
-
Select the files you have been looking for and click "Recovery".
-
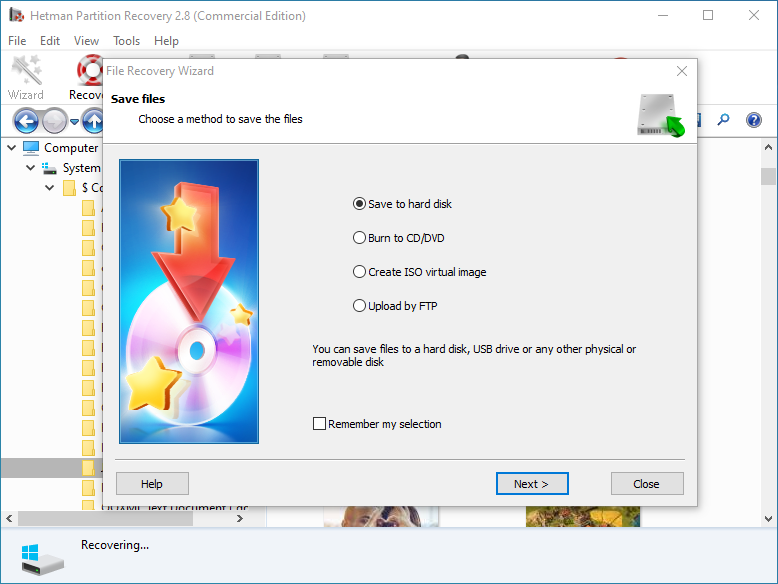
Choose one of the methods for saving the files and recover them.
How to open file with ".TLS" extension?
Looking for how to open a stereo tuneUp Utilities Logon Screen image file file?
Programs that open ".TLS" files
| Windows |
|---|
|
|
Additional Information
-
File type: TuneUp Utilities Logon Screen
-
File extension: .TLS
-
Developer: TuneUp Corporation
-
Category: Misc Files
-
Format: Binary



